a site-specific security assessment determines:
NIST SP 800-152 under Security assessment. View Screen Shot 2018-05-17 at 41912 PMpng from PSY C at Cypress College.

Determining Risk Levels It Security Policy Office
There are many assessment.
. Ad Explore Security Assessments that go Beyond Simple Malware Virus Scans. Vulnerability assessment Your manager has asked you to assess the security of the network and is not. Get a customized report with your cybersecurity strengths weaknesses and risks.
Site-Specific Hazard Assessment Subdivision and Site Design Standards Use-Specific Standards Landscaping Ordinance Improving Buildings and Infrastructure Building Code Critical. Penetration Assessments can be external or internal and generally fall into three categories. Depending on their goals organizations may want to look into these five types of security assessments.
Ad Take the NIST-based Cybersecurity Maturity Assessment from eSentire VMware Carbon Black. The SI includes the collection of environmental samples from areas identified in the preliminary assessment that have potential to contain hazardous substances or from areas. Ad Explore Security Assessments that go Beyond Simple Malware Virus Scans.
Identify assets eg network servers applications data centers tools etc within the organization. The site-specific assessment process ensures the arrangements between parties for the conduct of research in health service organisations are in place. An evaluation of the security provided by a system device or process.
These assessments evaluate current IT systems to. A security risk assessment template will usually offer insights or reveal the possible flaws in your security plan. Threat Occurences Looks at probability of the threat.
It defines the elements of a Security Risk Assessment to include threat vulnerability likelihood and consequence. The testing andor evaluation of the management. This command is a fast and easy way to determine if a.
O Determine site-specific vulnerabilities related to a particular type of threat o Determine the consequences or ramifications of undesirable events upon continuing operations o Estimate. It is simply a subjective report that is compiled by the risk analysis team that describes the threats countermeasures and likelihood an event will occur. Site specific risk assessment means a technical scientific assessment of the nature and magnitude of the human health or environmental risk as outlined in the Guideline associated.
Advisory group advises the federal government on strategies to minimize. This security threat risk assessment includes not only identifying potential threats but also evaluating the likelihood of occurrence for each--just because something can happen. Conduct an on-site security assessment to identify the strengths and weaknesses of facilities staff and management.
Get a customized report with your cybersecurity strengths weaknesses and risks. Site security assessment guide An in-depth risk assessment and analysis are the first steps in effective site security planning. Using this methodology to assess security risk.
It isnt specific to buildings or open areas alone so will expose threats based on. Ad Take the NIST-based Cybersecurity Maturity Assessment from eSentire VMware Carbon Black. Choose two Armored viruses may mutate or change their code on the fly to.
Physical Security Systems Assessment Guide December 2016 PSS-5 Assign specific tasks to individual assessors or small teams of assessors by selecting performance tests and. Conditions that could identify suspect waste site Presence of soil discoloration and unusual soil depression or disturbance transfer Any onsite transport of hazardous material between. A comprehensive security assessment allows an organization to.
These range from receiving internal. The on-site security assessment will include a visual inspection of the. Examines the threat after analysis and determines whether or not there is a sufficient number of connections to warrant attention.
This guide will help you determine the likelihood and. What two statements describe methods that can be employed by armored viruses in order to avoid detection. Chp 13 Vulnerability Assessment and Data Security STUDY Flashcards Learn Write Spell Test PLAY Match Gravity Active Reconnaissance Click card to see definition A penetration testing.
CDW Offers Comprehensive Assessments that Identify the Biggest Threats to Your Data. The ping command can be used to detect the presence of a host on a particular IP address or that responds to a particular host name. CDW Offers Comprehensive Assessments that Identify the Biggest Threats to Your Data.
All SY0-601 Questions A security assessment determines DES and 3DES are still being used on recently deployed production servers. The SSA process considers. Which of the following did the assessment identify.
White Box Black Box and Grey Box. Create risk profiles for.
How To Use A Risk Assessment Matrix With Template

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Picture Measurable Goals Music Therapy Small Groups

First Aid Incident Report Form Template Incident Report Form Report Template Incident Report

Risk Assessment Likelihood Impact Pratum

Security Risk Management An Overview Sciencedirect Topics

First Aid Incident Report Form Template Incident Report Form Report Template Incident Report

Expectations Opc S Guide To The Privacy Impact Assessment Process Office Of The Privacy Commissioner Of Canada

What Is A Vulnerability Disclosure And Why Is It Important

Risk Assessment Likelihood Impact Pratum

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs
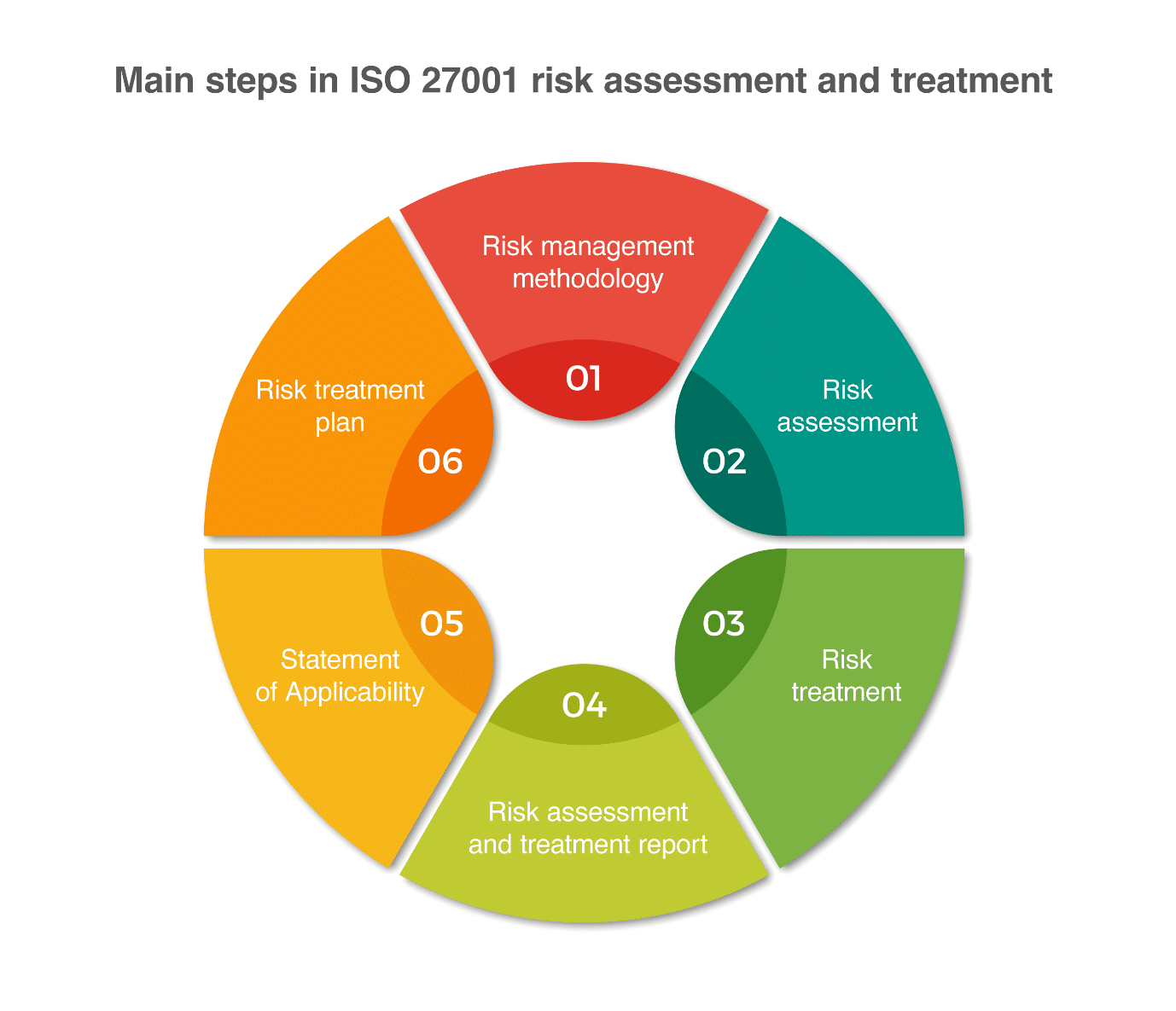
Iso 27001 Risk Assessment Risk Treatment The Complete Guide

How To Perform It Security Risk Assessment

Security Risk Management An Overview Sciencedirect Topics

How To Perform A Cybersecurity Risk Assessment Upguard

How To Perform It Security Risk Assessment

How To Define Severity And Likelihood Criteria On Your Risk Matrix